Table of Contents
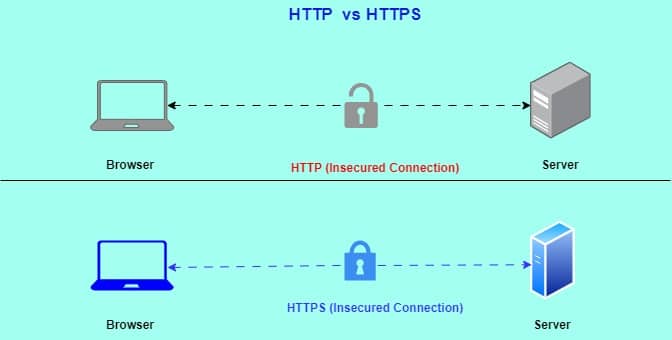
Key Differences:
- Client Hello: The browser initiates a connection by sending a “hello” message to the server, including supported cipher suites and the TLS version.
- Server Hello and Certificate: The server responds with its own “hello” message, selecting a cipher suite and sending its SSL certificate along with the public key.
- Certificate Verification: The browser verifies the server’s certificate against trusted Certificate Authorities (CAs). If valid, the browser generates a symmetric key, encrypts it with the server’s public key, and sends it to the server.
- Key Exchange: The server decrypts the symmetric key using its private key. Both parties now share the symmetric key, which is used for encrypting data during the session.
1. Confidentiality/Privacy
2. Integrity
3. Authentication
When it comes to SSL certificates, there are several options available, but three types stand out as the most popular and widely used: Single, Wildcard, and Multi-Domain SSL certificates.
- Single Domain SSL Certificates.
- Wildcard SSL Certificates.
- Multi-Domain SSL Certificates (MDC).
Single Domain SSL Certificates
Single Domain SSL Certificates are designed to secure a single domain name. It cannot be used to authenticate any other domain, not even subdomains of the domain it is issued for.

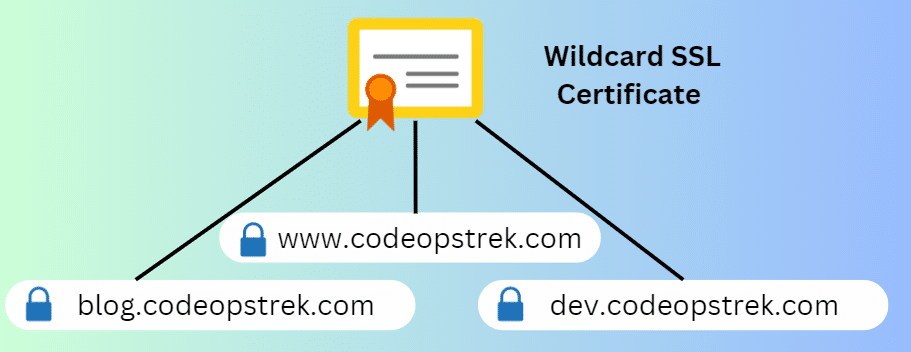
Wildcard SSL Certificates
Wildcard SSL Certificates offer more flexibility by allowing you to secure a primary domain and all its subdomains with a single certificate.
For example, if you have a website with multiple subdomains (such as blog.yourdomain.com, shop.yourdomain.com, etc.), a Wildcard SSL Certificate will cover them all.
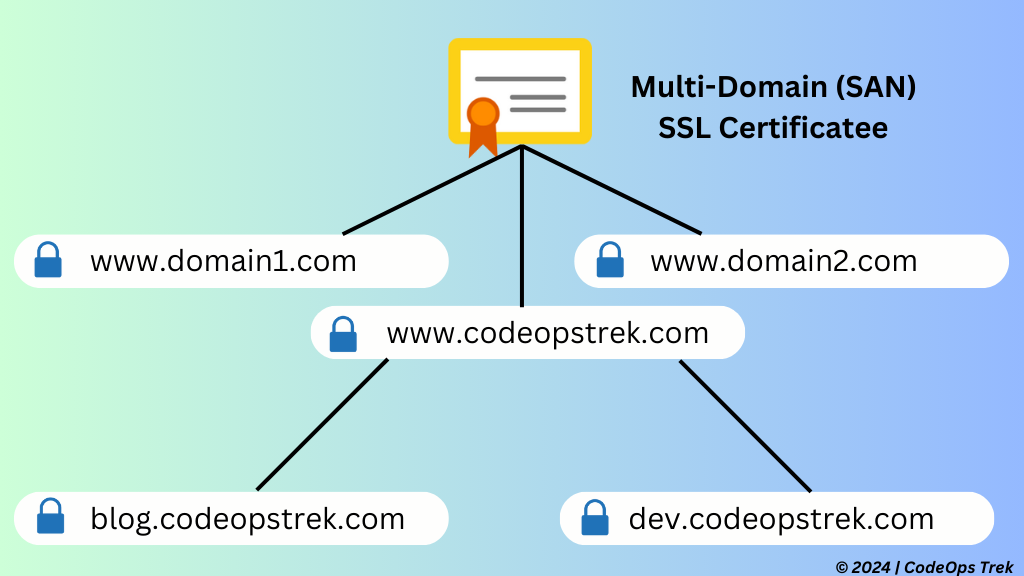
Multi-Domain SSL Certificates (MDC)
Multi-Domain SSL Certificates, also known as Subject Alternative Name (SAN) certificates, enable you to secure multiple domains and subdomains with one certificate.
Command to Generate a CSR:
openssl req -new -newkey rsa:2048 -nodes -keyout yourdomain.key -out yourdomain.csrYou will be asked some question
Country Name (2 letter code) [AU]: IN
State or Province Name (full name) [Some-State]: MH
Locality Name (eg, city) []: Mumbai
Organization Name (eg, company) [Internet Widgits Pty Ltd]: CodeOps Trek
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []: www.codeopstrek.com
Email Address []: contact@codeopstrek.com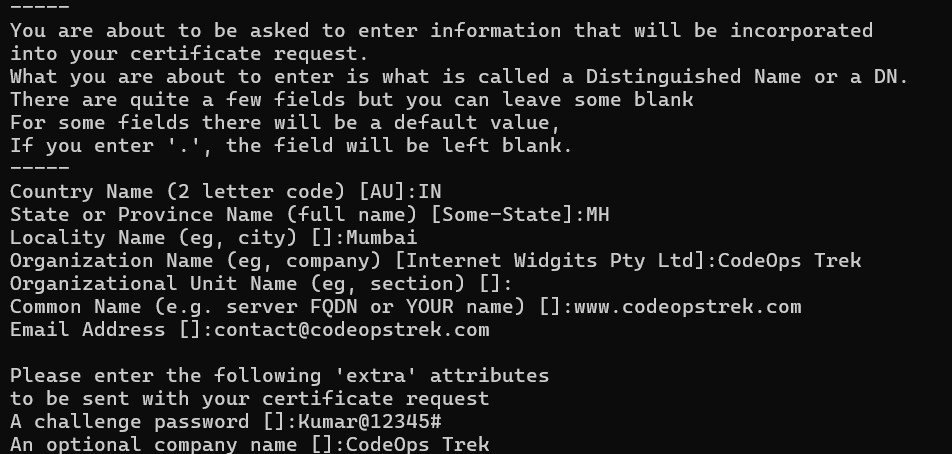
CSR & Key will generated in the folder.

Self-Sign the CSR
Run below command in the terminal of same folder where csr & key available.
openssl x509 -req -days 365 -in yourdomain.csr -signkey yourdomain.key -out yourdomain.crt

Self-signed certificates are used primarily for testing, development, and internal purposes. They are ideal for securing communications within private networks, development environments, and internal applications where trust from a public Certificate Authority (CA) is not required. Unlike certificates issued by a CA, self-signed certificates are signed by the entity’s own private key, making them cost-effective and immediately available. They are commonly used for:
- Testing and Development: To simulate SSL/TLS encryption in a development environment.
- Internal Networks: To secure internal communications without the need for a publicly trusted certificate.
- Learning and Training: To practice and understand certificate management without incurring costs.
Learn how to integrate self-signed SSL into Nginx web server easily.
Despite their benefits, self-signed certificates should not be used for public-facing websites or applications because they won’t be trusted by web browsers and can expose users to security risks.
Other Resources
Enhance your SSL/TLS management with the SSL Checker Tool by WebsitePlanet.
Features:
- SSL Certificate Details
- Server Details
- Certificate Chain Validation
- Report Download
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols for secure communication over networks. TLS is the successor to SSL, offering improved security and modern encryption algorithms.
SSL (Secure Sockets Layer) can be used to secure websites (HTTPS), emails, VPNs, file transfers, APIs, IoT communications, database connections, and online payments.
openssl req -x509 -newkey rsa:2048 -keyout server.key -out server.crt -days 365
The validity of a self-signed certificate is determined by the issuer and can typically range from a few months to several years. Commonly, self-signed certificates are set to expire in 1 year (365 days), but the validity period can be customized during creation
Self-signed certificates cannot be verified through traditional Certificate Authorities (CAs), but can be verified using their own public key.
CA stands for Certificate Authority. It is a trusted entity that issues digital certificates used to verify the identities of organizations, websites, and individuals on the internet.
Yes, a self-signed certificate can encrypt data, enabling secure communication between the server and client using its own public key infrastructure, though it lacks validation by a third-party Certificate Authority (CA).
At CodeOps Trek, we are dedicated to providing solutions and building robust code architectures. Integrating NGINX into your web stack is a vital step toward achieving these goals. Stay tuned for more in-depth guides on software development, and happy coding!
